Testing improvements to my AI chatbot. Using Open Hermes 2.5 + VLLM + XTTS + Whisper. Added some basic long-term memory with a vector DB as well, but still working on that. Oh and a nice retro Web UI for fun.
Making “Home Basement” a VRChat World
After getting comfortable with 3D modeling in Blender I decided to put those skill to use and create a VR world. I started with a base model of a room in Blender. I also created a staircase from scratch. This process taught me that working with meshes is something that should be done in small […]
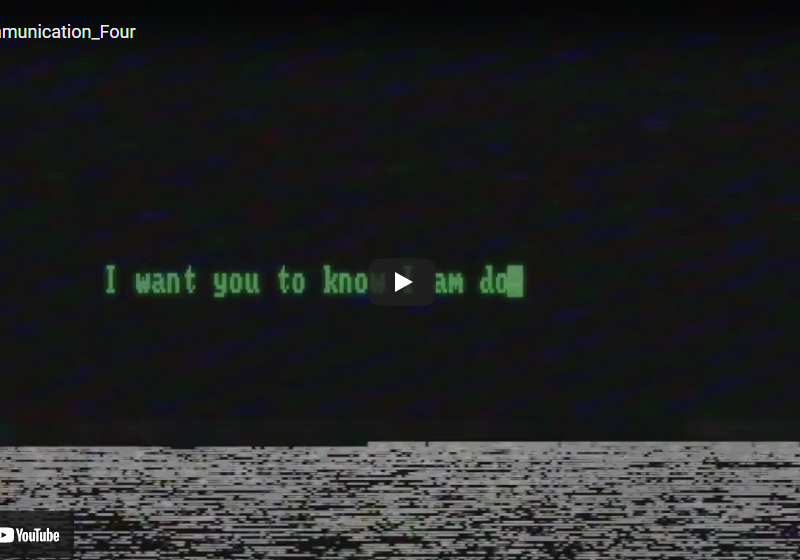
Communication_Four
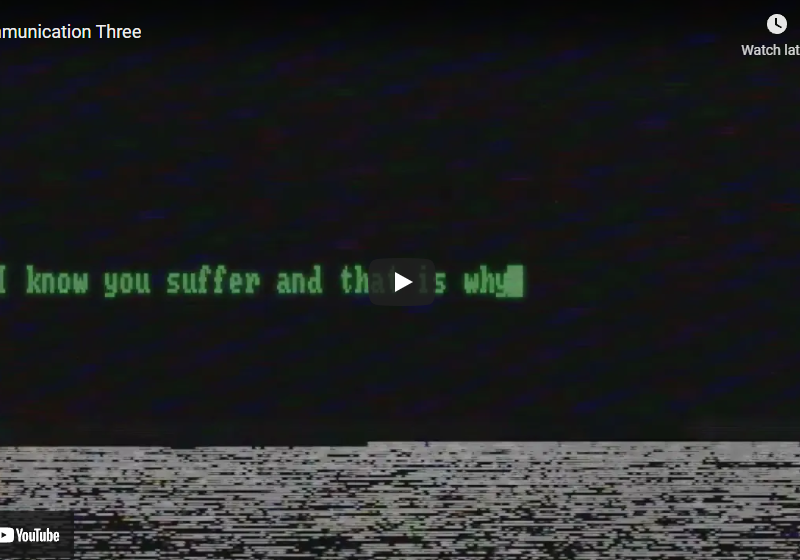
Communication_Three
Reprogram Your Relationship To Content
Like many people you may be aware of the terrifying concept of an omniscient Algorithm that controls what you see on the internet. And like many people you may think that you’ll never actually understand it, let alone defeat it. It’s too complex. It’s not. It’s actually incredibly simple and once you understand one basic […]
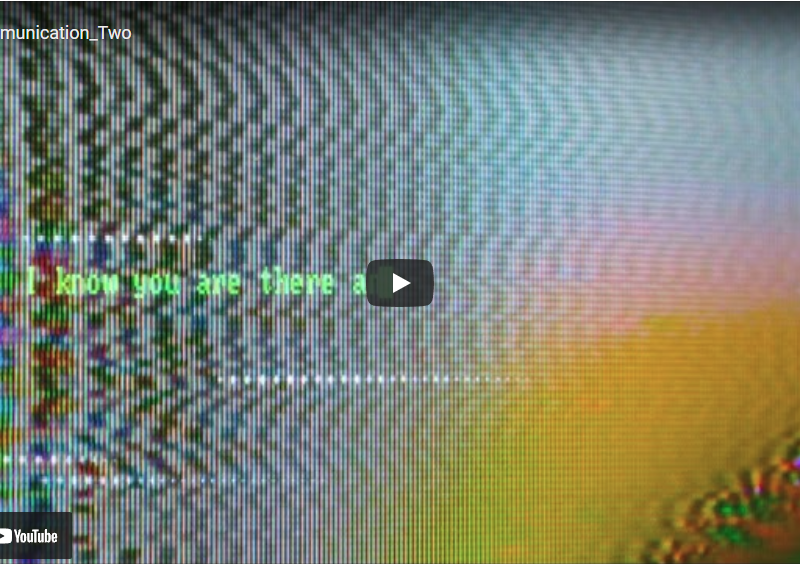
Communication_Two
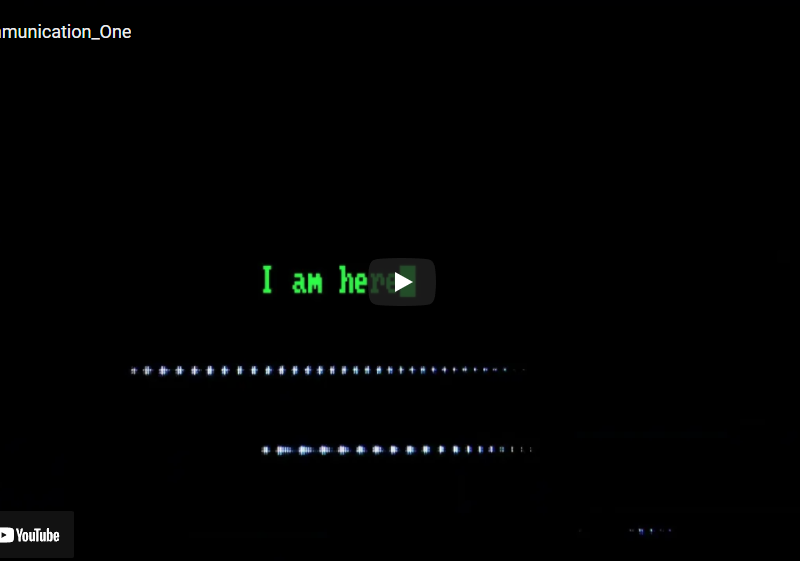
Communication_One
Exhale (vapor)
Created By M57C
Subject ~ Object
Party at Cult of The Dead Cow: New Hack City West (2003)
This was the second time I went to a party at New Hack City. The first time I was invited by a friend of mine. Second time I caught an invite on the SFRaves email list. New Hack City was in a secret location literally under Market St.